More than 85 million Android devices worldwide have been taken over by the Yingmob, a group of China-based cybercriminals who created the HummingBad malware, according to a Check Point report released last week.
HummingBad establishes a persistent rootkit on Android devices, generates fraudulent ad revenue, and installs additional fraudulent apps.
If it fails to establish a rootkit, it effectively carpet bombs the target devices with poisoned apps.
HummingBad has been generating revenue of US$300,000 a month, according to Check Point.
The malware runs along with legitimate ad campaigns that Yingmob has produced for its legitimate ad analytics business.
“We’ve long been aware of this evolving family of malware, and we’re constantly improving our systems that detect it,” a Google spokesperson said in a statement provided to TechNewsWorld by company rep Aaron Stein. “We actively block installations of infected apps to keep users and their information safe.”
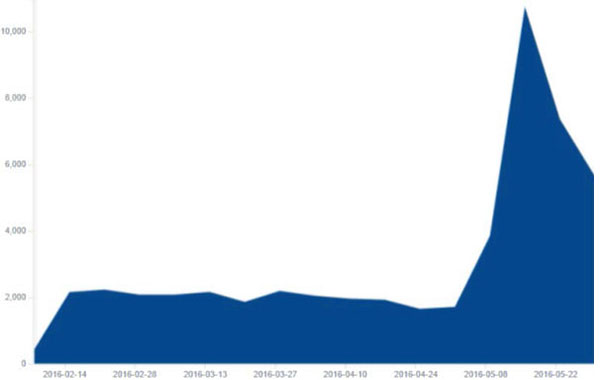
HummingBad’s Victim Count
About 25 percent of the roughly 200 apps on the control panel of Umeng — a tracking and analytics service HummingBad’s creators use — are malicious, Check Point said. An estimated 10 million people have been using those malicious apps.
China and India have the highest number of victims — 1.6 million and 1.3 million, respectively. The Philippines comes in third with 520,000. The United States is eighth, with 286,000 victims.
KitKat runs on 50 percent of the affected devices, Jelly Bean on 40 percent, Lollipop on 7 percent, Ice Cream Sandwich on 2 percent, and Marshmallow on 1 percent, according to Check Point.
How HummingBad Works
HummingBad uses a sophisticated, multistage attack chain with two main components.
The first component, SSP, uses a rootkit that exploits multiple vulnerabilities to try to root the target device.
SSP injects a library into the Google Play process using ptrace, Check Point said, which lets HummingBad imitate clicks on install/buy/accept buttons inside Google Play.
If rooting fails, the second component, CAP, installs fraudulent apps using elaborate techniques. It decrypts module_encrypt.jar from its assets when it launches on a device, then dynamically loads code containing the main malware functionality. Next it decrypts and runs a native daemon binary, among other things.
Regardless of whether the rooting succeeds, HummingBad downloads as many fraudulent apps to the target device as possible — a blend of several malicious components, many of them variations with the same functionality.
HummingBad Risk
HummingBad “is very hard to identify, very difficult to get rid of, and massively invasive,” said Rob Enderle, principal analyst at the Enderle Group.
“Alphabet has had a very poor reputation with regard to security, and it will be watched closely to see how quickly and permanently it can mitigate this exploit,” he told TechNewsWorld.
“If done too poorly or slowly, it could quickly turn Android into an unacceptable risk for the entire industry.
HummingBad could stymie Google’s plans to embed Android more deeply into the auto industry, Enderle noted. Google has effectively built a car infotainment system into Nougat, the latest version of Android, he pointed out, and HummingBad “could easily have adverse implications with regard to driver safety.”























































