Apple on Wednesday released Security Update 2017-001 to fix a serious flaw revealed earlier via Twitter. The patch is available for macOS High Sierra 10.13.1. macOS 10.12.6 and earlier versions aren’t affected by the flaw.
“This morning, as of 8 a.m., the update is available for download, and, starting later today, it will be immediately automatically installed on all systems running MacOS High Sierra 10.13.1,” Apple said in a statement provided to TechNewsWorld by company spokesperson Todd Wilder.
“We greatly regret this error and we apologize to all Mac users, both for releasing with this vulnerability and for the concern it has caused,” the company said.
Internet Uproar
The MacOS High Sierra flaw allowed anyone take over a Mac, coder Lemi Orhan Ergin, founder of Software Craftsmanship Turkey, disclosed in a tweet to Apple Support on Tuesday.
Dear @AppleSupport, we noticed a *HUGE* security issue at MacOS High Sierra. Anyone can login as "root" with empty password after clicking on login button several times. Are you aware of it @Apple?
— Lemi Orhan Ergin (@lemiorhan) November 28, 2017
Attackers could log in as “root” with an empty password after clicking repeatedly on the login button, Ergin discovered.
The tweet sparked a storm on the Internet.
Many responders to Ergin’s tweet said they encountered the problem on testing their machines, but Michael Linde said otherwise.
Um, not on High Sierra machines at my work – are you sure that isn’t someone’s management setup (as bad as that is)?
— Michael Linde (@mlinde) November 28, 2017
Perhaps Linde was one of the fortunate few — @unsynchronized tweeted that the bug allowed other attacks.
macos 10.13 bug isn't limited to root in all circumstances; via ARD, you can log in as any existing user (e.g. _applepay) and share the screen of the logged-in user. also _uucp is allowed to log in
— cstone (@unsynchronized) November 28, 2017
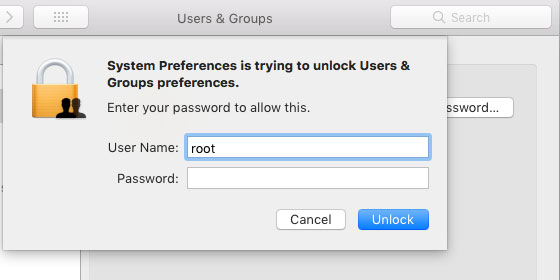
In response to an apparent request from Apple Support, Ergin said the flaw could be accessed by gong to System Preferences>Users & Groups.
“Click the lock to make changes,” he tweeted. “Then use ‘root’ with no password. And try it for several times. Result is unbelievable!”
Apple Support then asked Ergin to send a DM including his Mac model and the version of macOS used.
The Threat Posed
It could be argued that the danger of the flaw might have been overstated. Attackers would have needed physical access to target machines unless Remote Desktop was enabled, but enterprises that enable Remote Desktop are likely to have strong cybersecurity fences.
“Certainly there are more significant vulnerabilities out there, but any time you’re talking about root access, that shouldn’t be taken lightly,” said Jesse Dean, senior director at Tetrad Digital Integrity.
“It was exploitable remotely if the firewall didn’t block remote access services,” he told TechNewsWorld, such as “Apple Remote Desktop and virtual network computing.”
Apologies Might Not Suffice
Although Apple issued a patch, it had not sent a push notification to users as of Wednesday afternoon.
Savvy users can go to the App Store, check the Updates section, and download and install the patch. Others can wait for Apple to push out the update, but the delay might put people at risk.
“It would have been a good gesture to show they can move quickly and that they care about security and their customers,” Dean observed. “By not sending notifications, it appears they’re taking a different approach and letting other news, like AWS Re:Invent, dominate.”
On the other hand, “That’s a business decision they weighed and made,” he remarked. “While the vulnerability is a big deal and allows root access, it’s relatively less critical than having the same issue on an enterprise router or server, for example.”
Good Coders Gone Rogue?
There’s an established process for hackers who find a flaw: They first notify the vendor, then wait a given number of days, and, if there’s no response, publicize the flaw for the greater good.
It’s not clear whether Ergin followed that protocol.
His action “wasn’t the best approach or in line with established protocol,” Dean said. “On one hand, it’s good to get the word out; however, if there’s no known fix, publicizing the vulnerability in such a way doesn’t support the greater good.”
























































Mac OS "High" Sierra is a joke, its a terrible beta. Many hardware and software issues with it. The "Server" version lol, AM azing, they have removed File Sharing in the actual app, and removed iOS/WebDAVS support (which I use daily to have cross platform support on mobile and desktop systems). Even though their iOS 11 has the Files app, which clearly has full support for Mac OS Server, it cant be used with 10.13, 10.12.6 and 10.11.6 work perfectly with it. Apple, concentrating too much on phones/watches/TV and have lost sight of the computer hardware/software