Security-minded internet users looking for another layer of obscurity when traveling in cyberspace can have it with some new tech announced Monday by Atlas VPN.
The paid VPN service has introduced a new way to route internet traffic, called MultiHop+, that’s more secure and private than conventional methods. It does that by allowing users to connect to the internet through several rotating VPN locations simultaneously.
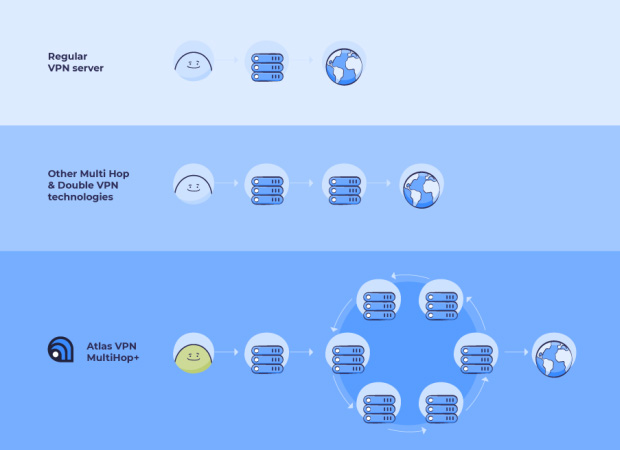
With a traditional VPN, a “tunnel” is created between a user and a VPN server. All traffic in the tunnel is encrypted to protect its privacy. Interaction with the internet is done from the VPN server, which masks a user’s true IP address and real identity.
The problem with that method is it’s still possible to track down a VPN user by correlating the connectivity to a VPN endpoint with traffic out of the endpoint. “Multihop enables a layer of ambiguity where such correlation becomes more difficult,” John Bambenek, a principal threat hunter at Netenrich IT, a digital security operations company in San Jose, Calif., told TechNewsWorld.
With MultiHop+, a user’s internet traffic is sent to several VPN servers simultaneously. That protects the traffic with an additional layer of encryption and hides their identity behind multiple IP addresses from different geographical locations.
MultiHop+ is available with a premium subscription to Atlas VPN.
“MultiHop works similar to the Tor network which makes it very hard to trace online activity back to an individual user,” Jason Hicks, field CISO and executive advisor at Coalfire, a provider of cybersecurity advisory services in Westminster, Colo., told TechNewsWorld.
Boon for Activists
Tor is free and open-source software for enabling anonymous communication on the internet. Used to access the dark web, it uses a free, worldwide, volunteer overlay network, consisting of more than 6,000 relays, to conceal a user’s location and usage from traffic snoopers.
Like the Tor network, the servers within the Atlas VPN MultiHop+ chain are selected randomly. What’s unique to MultiHop+, though, is that the exit server rotates throughout the browsing. That means that each time a user accesses a different domain, their traffic takes a new and random route through the network, which makes it near impossible to predict and track.
“While regular VPN servers are enough for most internet users, people living in highly censored countries, as well as journalists and activists, can highly benefit from added protection,” Atlas VPN PR Manager Ruta Cizinauskaite said in a news release.
“Currently, users can choose from two MultiHop+ server chains, including Europe and North America,” she told TechNewsWorld.
Hicks agreed that reporters and activists in countries with oppressive regimes could benefit from MultiHop+. “If state security services were able to track them down via their traffic and identify them, it could have serious implications for their physical safety,” he explained.
“Typically this is marketed to people concerned about government surveillance,” added Bambenek, “perhaps even those who are concerned about the ubiquitous monitoring by surveillance capitalists that have branded themselves as tech companies.”
Potential for Abuse
While MultiHop+ offers the benefits of Tor, it does so without some of the drawbacks of the open-source technology. “It presumably offers a similar layer of privacy as Tor without the suspicion that traffic from Tor end nodes generates,” Bambenek said.
“Many organizations will block Tor but allow inbound connects from VPN endpoints,” he explained.
Since Atlas VPN is a paid service, it should produce a better and faster user experience than a free VPN service or Tor, Hicks maintained. However, he added, “This method likely would increase the latency of your connections as your traffic needs to transit multiple servers and is being encrypted multiple times.”
MultiHop+ can create another problem for users. “The people who need to be most concerned about network surveillance are also the ones most likely to be apprehended and prosecuted for using it in the first place,” Bambenek said. “Many high-surveillance jurisdictions overtly outlaw the use of VPNs, while others use it as a cause for suspicion.”
Despite the laudable reasons for designing ways to preserve the privacy of internet users, there’s always the possibility that they can be abused. “Any technology developed for any purpose in any industry can and will be abused by criminals,” Bambenek observed. “That said, criminals already have their VPN tools.”
Hicks agreed that anything that can make traffic undetectable will be utilized by cybercriminals. “However,” he added, “there are already multiple options available for them so this is not a unique offering.”
On the other hand, he noted, “This service makes it simple to route your traffic through multiple hops so it could enable less technically sophisticated attackers to utilize this method.”
Cards Stacked Against Privacy
While a multi-hop VPN offers more security than a traditional VPN, it isn’t the final word in secure VPNs. “Multi-path VPNs add a whole other level of security by actively dispersing the flow of information simultaneously over multiple paths, thereby making the payload virtually impossible to detect and capture,” maintained Rajiv Pimplaskar, CEO of Dispersive Holdings, a Secure Access Service Edge provider in Roswell, Ga.
“The multi-path approach can improve not just security, but also reduce latency and improve application response times improving the user experience,” he told TechNewsWorld.
“Furthermore,” he continued, “today’s geopolitical conditions necessitate increased communications security, not just for internet access, but also site-to-site, site-to-user and user-to-user. Multi-path VPNs can create an any-any mesh fabric that can make the solution relevant not just for consumers but also business users.”
However, Ron Bradley, vice president of Shared Assessments, a provider of tools and certifications for third-party risk management in Santa Fe, N.M. believes that no matter what lengths an individual goes to protect their online activity, the cards are stacked against them.
“The internet works on a few basic principles which are indisputable,” he told TechNewsWorld. “TCPIP and virtual private networks are great for encrypting information and giving users a sense of security and anonymity, but at some point, in order to get your information from point A to point B, your network traffic has to communicate via DNS servers and network routers.”
“The cybersecurity capability of nation-states gives them the ability to know who you are, where you are, and what data you are sending or receiving,” he said. “Nothing we do on the internet is private or secret. Your data can be compromised, given enough resources.”


























































