
Following Edward Snowden’s revelations about indiscriminate government snooping on U.S. citizens, many Net surfers would like to find a way to lower their visibility on the Internet. There are a number of tools in cyberspace that can help a soul do that, but they can take time and savvy to set up. That’s why Kerry Cox launched the Sierra Project.
The project, which he hopes to fund through Kickstarter, aims to provide consumers with a way to anonymously wander the Net, as well as encrypt all their network traffic.
Designed to be a plug-and-play device, the Sierra unit sits between you and the Internet and obscures your identity. In its promotional material, the project explains that most cyberattacks are directed at where you access the Net, or your IP address. When you enter the Net through the Sierra device, your traffic is sent to the project’s servers. That way only the Project Sierra server IP is visible to the world.
The proxy system protects your data from being vulnerable to traffic analysis, which allows hackers and other third parties to access information about your location, spending habits and behavior.
“The days of just being able to use a firewall are over with, because the firewall doesn’t protect traffic going out,” Cox told TechNewsWorld. “At the very least, you have to have your IP address masked.”
Better Than Software
While there are software solutions that promise to protect Web surfing from snoops, they fall short of what the Sierra project can do, Cox maintained.
“Software solutions only encrypt Web traffic,” he explained. “I’m not trying to encrypt just Web traffic. I’m trying to protect all traffic on a home network.”
That includes multiple devices. Cox has operated as many as 13 devices through his Sierra device, he said.
“Software solutions can give you a false sense of security because you’re encrypting your traffic on your browser, but you’re not protecting your network from attack,” he pointed out.
Another drawback to software solutions is that many times you have to pay for individual licenses. So if you have multiple devices, that means multiple cash outlays — and if the software works on a subscription basis, that’s multiple cash outlays annually.
Cox’s hardware solution, though, is not without problems. For example, the Sierra servers are geographically distributed. If your Sierra device, due to traffic demands, routes your traffic to Germany and you live in California, you could experience performance issues.
In addition, since you’re hiding your identity, you’ll be forced to login to websites that ordinarily would welcome you with open arms.
Nevertheless, many of those snags can be worked out before the device is finalized, Cox said. “They aren’t showstoppers.”
True Ephemeral Photos
Snapchat made its reputation on being able to share photos for short periods of time. It found picture sharers loved the Mission: Impossible effect of self-destructing images in a short period of time.
Of course, the blush rubbed off the app when it was discovered the photos could be preserved with a simple screen capture. ContentGuard, though, thinks it has an answer to the screenshot problem. It’s an iPhone app called “Yovo.”
The free app is similar to other ephemeral photo programs. You take a shot, maybe add some text to it, send it to a friend, they display it, and it self-destructs.
“We felt there was a gap between completely closed and completely open and live forever, and that became the genesis of Yovo,” ContentGuard Chief Product Officer Scott Richardson told TechNewsWorld. “The question we were trying to answer was can a privacy app also be social.”
To preserve privacy, the screen capture problem would have to be addressed. To do that, the company invented D-Fence. The filter recreates the optical effect of looking through a slatted fence while traveling parallel to it very fast.
To your eye, you appear to be seeing an unfiltered image, but in fact, the image is appearing between virtual “slats” so if you try to perform a screen capture, you’ll get more slat than photo.
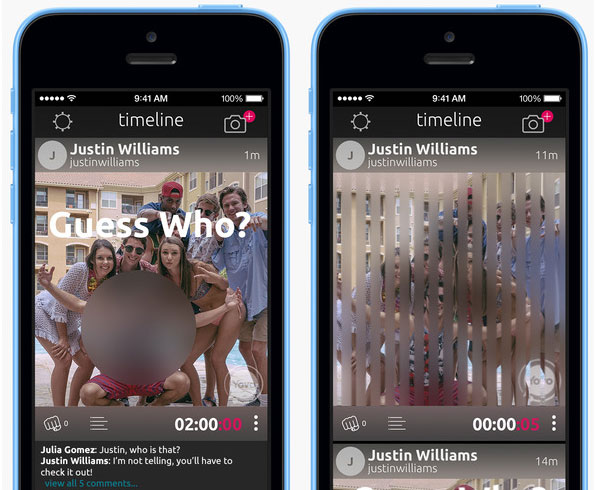
Yovo also lets you share images outside the app. The images are blurred, though, so if someone wants to see a pristine version of a photo, they have to install the app on their phone. “It helps us in on-boarding users,” Richardson explained.
Solid State Self-Destruction
Solid state drives have many benefits. They’re fast. They don’t have any moving parts to break. They don’t crash. They have a big drawback, too. It’s difficult to scrub data from them.
That’s why SecureDrives has introduced its Autothysis line of solid-state drives. The 128-GB drives have GSM built into them so they can be destroyed via SMS message.
And when SecureDrives says destroyed, it means destroyed.
“We physically break it into pieces,” SecureDrives CEO James Little told TechNewsWorld. “That’s the uniqueness of this drive. It has the same effect as taking a hammer to it.”
The drives, which sell for US$1,563 and $1,660, are aimed primarily at intelligence agencies and the military.
“We are also getting interest from corporates and high net-worth individuals,” Little said, “people that want to destroy a drive on demand.”
Breach Diary
- Oct. 13. Dropbox denies usernames and passwords of some of its users posted to the Internet by hackers were obtained through a breach of its systems. The data was stolen from unrelated services, Dropbox said.
- Oct. 14. Microsoft patches Windows bug that’s been used by Russian hackers since August to spy on computers used by NATO, the European Union, Ukraine and companies in the energy and telecommunications sectors.
- Oct. 14. OpenSSL Project issues advisory about “Poodle” vulnerability in SSL 3.0, which could be exploited by an attacker to hijack browser sessions on public WiFi networks.
- Oct. 14. Atlanta Business Chronicle reports at least 21 lawsuits have been filed against Home Depot over data theft revealed in September of credit card information of some 40 million customers.
- Oct. 14. Lawsuit filed in New Mexico state court against Community Health Systems over data theft in August of nonmedical records for 4.5 million patients.
- Oct. 14. Canadian Wildlife Management Branch reports personal information of some 15,000 people is at risk after agency’s website was accessed by an unauthorized user.
- Oct. 16. FBI Director James B. Comey at Brookings Institue says post-Snowden pendulum has gone too far and called for new laws and regulations to force companies to create ways for governments to unlock photos, emails and contacts stored on mobile phones.
- Oct. 16. Ponemon Institute reports annualized cost this year of cybercrime per U.S. organization to be $12.7 million, a 9.3 percent increase over 2013.
- Oct. 17. TD Bank agrees to $850,000 multistate settlement in case involving data breach in 2012 in which 1.4 million files containing personal information for 260,000 customers were compromised when some unencrypted backup tapes were lost.
Upcoming Security Events
- Oct. 19-27. SANS Network Security 2014. Caesar’s Palace, Las Vegas, Nevada. Courses: job-based, $3,145-$5,095; skill-based, $1,045-$3,950.
- Oct. 29. How to Best Secure Your Mobile Enterprise. 3 p.m. ET. Webinar sponsored by Dell. Free with registration.
- Oct. 29-30. Security Industry Association: Securing New Ground. Millennium Broadway Hotel, New York City. Registration: before Oct. 4, $1,095-$1,395; after Oct. 3, $1,495-$1,895.
- Oct. 29-30. Dallas SecureWorld. Plano Centre, 2000 East Spring Parkway, Plano, Texas. Registration: $695, two days; $545, one day.
- Nov. 5. Bay Area Secureworld. Santa Clara Convention Center, Santa Clara, California. Registration: $695, two days; $545, one day.
- Nov. 5. FedCyber 2014 Annual Summit. Tyson’s Corner Marriot, 8028 Leesburg Pike, Tyson’s Corner, Virginia. Registration: free, government; $106.49, academics; $626.92, industry.
- Nov. 6. B-Sides Iceland. Tjarnarb, Reykjavk, Iceland. Free.
- Nov. 8. B-Sides Dallas-Fort Worth. University of Texas-Dallas (UTD), ECSS building, 800 West Campbell Rd, Richardson, Texas. Free.
- Nov. 12-13. Seattle Secureworld. Meydenbauer Center, Seattle. Registration: $695, two days; $545, one day.
- Nov. 15. B-Sides Jacksonville. The Sheraton Hotel, 10605 Deerwood Park Blvd., Jacksonville, Florida. Free.
- Nov. 19. Stealing from Uncle Sam. 7:30 a.m.-1:30 p.m. ET. Newseum, Washington, D.C. Registration: government and press, free; before Nov. 19, $495; Nov. 19, $595.
- Nov. 21-22. B-Sides Charleston. College of Charleston campus, Charleston, South Carolina. Free.
- Nov. 22. B-Sides Vienna. Top Kino, Rahlgasse 1 (Ecke Theobaldgasse, 1060 Wien, Vienna, Austria. Free.
- Dec. 2-4. Gartner Identity & Access Management Summit. Caesars Palace, Las Vegas, Nevada. Registration: before Oct. 4, $2,150; after Oct. 4, $2,450; public employees, $2,050.
- Dec. 8-11. Black Hat Trainings. The Bolger Center, Potomac, Maryland. Course Registation: before Nov. 1, $2,500-$3,800; before Dec. 6, $2,700-$4,000; after Dec. 10, $3,800-$4,300.





















































You don’t need to wait for a special device. Pick up a Netgear WNR3500Lv2 (usually sold as a N300, make sure its v2) and install Tomato on it. Its pretty easy to do. Go to MyOpenRouter.com and download the "Shibby Tomato all-in-one" package. Plug in your Netgear and connect to its admin interface. Select software update and upload the file you downloaded. Reboot and perform a factory reset. Then log back in and setup TOR. These are summarrized instructions, but it really is that easy.
Although I haven’t used it for TOR (I use OpenVPN, OpenDNS, DDNS updates and specialized firewall rules) everything else I’ve done is so well thought out and highly functional that I imagine going TOR is only a matter of flipping a switch.
I’ve been involved with building about a dozen of these routers and my experience with them has been fantastic. Its replaced my dedicated Linux firewall machine, with OpenVPN, firewall filters, OpenDNS, with DDNS updates, IPv6 tunnels, … Its AM azingly easy to setup. I’ve actually thought about reselling these built this way.
I would like to mention though: As the Sierra Project points out about other security solutions, this is not a *COMPLETE* solution, and I doubt theirs is either. A firewall is part of it. Using an anonymizer is part of it. But other activities that you perform on the net leave their own foot prints. So watch yourself out there.
Also its worth noting that their are other Tomato firmware builds offered by Shibby that have less features (ie: less to secure). You can follow the links from the MyOpenRouter site and download one of those if you prefer.
And although I think it goes without saying: I’m not responsible for what you do to your device(s).