Internal documents recently leaked by a member of the Conti ransomware group reveal the gang’s status as a multi-layered business organization.
Researchers at BreachQuest, a cybersecurity and incident response firm in Dallas, on Wednesday published its analyses of chat logs a disgruntled group member posted first on private channels and then on Twitter several weeks ago. The leaks followed an aggressive pro-Russian message on the well-known ransomware group’s website.
The release is intended to help organizations understand the inner workings of Conti’s organizational infrastructure, according to Marco Figueroa, head of product at BreachQuest and former principal threat researcher at SentinelOne.
These chat logs present a deep dive into the ransomware gang’s revenue numbers, leaders, recruiting practices and operations, and victims.
One of the most surprising revelations is the group’s top leader heavily investing in bitcoin and creating its own blockchain network to support the Conti group. Another key revealed from the chat conversations is that nearly all group members reside in Russia, confirmed Figueroa.
“This is a well-oiled machine that has been running for a while. They made $50 million in September,” he told TechNewsWorld.
Chat Logs Overview
The Conti group previously announced it would execute cyberattack campaigns supporting Russia’s ongoing invasion of Ukraine.
According to BreachQuest, the infosec community then began circulating leaks provided by a Ukrainian security researcher that detail multiple years of internal chat logs revealing Conti’s operations.
The leaked logs show that Conti does not limit attacks to large companies or targets. They also go after small businesses.
One of Conti’s primary goals is to maximize victims’ cooperation in paying to decrypt their data through price negotiations, Figueroa said. The strategy includes a series of gradually larger data releases until the victims agree to pay. Until they do, each new release of compromised information has a higher price attached.
“One of the things that the blog reveals is that they want to honor their work,” he said.
Not included in BreachQuest’s blog on the log content was a discussion involving how one victim company made a special request in exchange for paying. The company wanted to download all its files and then delete Conti’s copies, according to Figueroa.
The chat logs disclosed the back-and-forth discussions and Conti’s agreement to comply as an indication that victims can trust Conti’s promises.
Well Organized
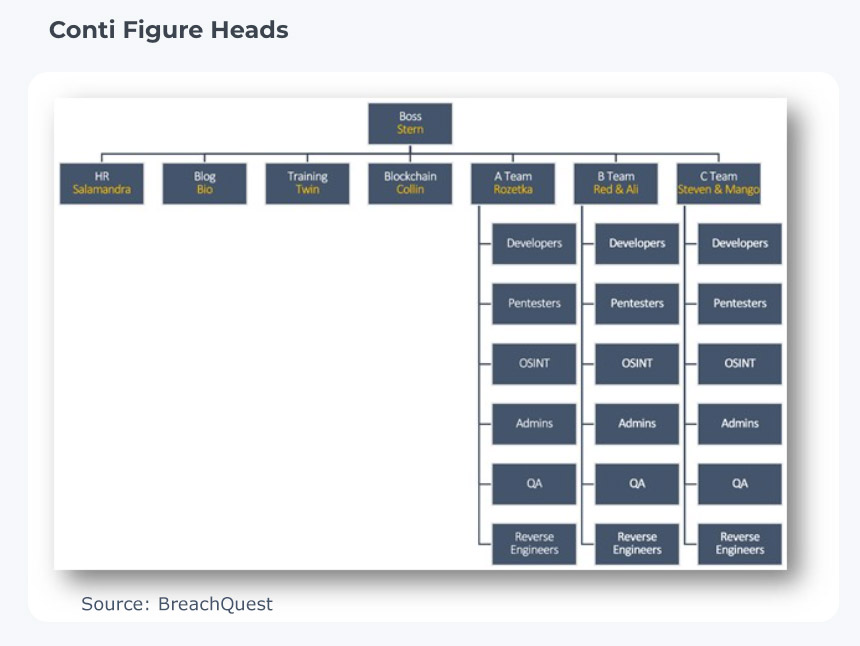
Conti is organized into an effective hierarchy that isolates its workers within skilled groups. Key leaders are identified with indistinct names and titles.
New hires’ work is kept vague to prevent them from understanding too much about the organization. This may be a contributing factor to the organization’s high turnover rate as well as the criminal nature of the work, notes BreachQuest’s report.
Conti divides teams into groups with an assigned team leader. Multiple leaders may work within large groups to maintain work assignments and training.
The workers are explicitly required to “Listen, Do, Learn, and Ask questions, Follow the guides and instructions, complete the assigned tasks.”
The Conti leaks and the ongoing war in Ukraine may push Conti’s leaders to intensify recruiting efforts. The devalued ruble and international sanctions against Russia are shifting Russians to bitcoin. So, Conti pays via bitcoin as requested by workers, according to the leaked logs.
Recruiting Process
Conti recruits workers using several strategies. The primary method is recommendations from current trusted workers. Another method uses recruiting services to find candidates with the needed skill sets.
One such service is a Russia-based website which allows Conti’s HR department to access the resume database for potential qualified candidates. An analyzed chat between Conti staffers involves a significant price change by the website that is discounted to Conti.
Interviewing at Conti is problematic. Interviewees wait in a chat room and questions are answered via chat exchanges rather than video, because video could compromise operational security of its members. Many of the candidates leave the chat rooms before the interview begins.
The candidates passing the interview negotiate their salary terms and their role in the organization. Those hired go through “Newbie Induction Training.”
Operational Factors
Much of the backroom works involves hiring talent as full-stack, crypto, C++ and PHP developers. They create different tools like lockers, spamming, backdoor tools and/or admin panels.
Since many of the web applications were written in PHP, the released software was missing code and was almost impossible to get working. Programmers had to fix all this.
Reverse engineers analyze Microsoft updates to learn what changes come after system updates. They also reverse engineer endpoint protection products to bypass protection that may tamper or inhibit their success in any way.
Special teams look for targets by collecting information from openly available sources online with various techniques. Admins assist in managing compromised enterprise networks and collecting victim information critical to their business to extract the maximum amount of payment.
Testers help by evaluating and verifying that the Conti tooling does what it is supposed to do in specific environments. The chat logs reveal the daily Windows Defender signature test to ensure that Conti’s tools would not be detected.
Conti follows specific proven processes to ensure a foothold into a compromised network. The hacker group looks for potentially interesting people like an admin, engineer, or someone in IT.
Backups Prime Targets
Ransomware teams hunt for backup servers to encrypt the victim company’s data. Searchers also use techniques to bypass backup storage vendors to make sure the backups are encrypted.
Leaked logs show that Conti hunts for financial documents, accounting files, clients, projects, and much more. The strategy pushes Conti’s workers to understand that their success depends on getting the target organization’s information useful for convincing the victims to pay.
Relying on backup files in the cloud or elsewhere will not keep a targeted company or organization safe from compromise, noted Figueroa.
“They go after your backups. They will not do anything (to notify a company of the successful compromise) until they know they got you in a bind where you cannot get out,” said Figueroa.
The leaked chat logs and complete analysis are available on the BreachQuest website.



























































