Have you seen the recent television commercial that shows the Pentagon and says, “This building gets attacked 3 million times a day.” The sad news is that it’s true.
Cyber-warfare and cyber-attacks have now become a reality. Ever consider how your business would be impacted if the Internet went away for an hour, a day or an even a longer period of time? Businesses, governments and industries have all become dependent on the Internet as a primary channel for businesses. They buy, sell and support their customers as well as their employees over the Internet. Given the significant role the Internet plays in our society and economy, it has become a primary target for attack by nation states and terrorists.
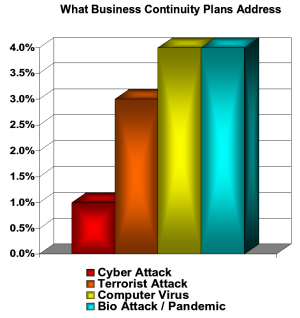
At this time, more than 120 countries and at least four terrorist groups have active cyber-weapons development programs in place. Are you ready for a cyber-attack? The answer is likely no, according to the Director of National Intelligence Mike McConnell. Many business leaders are unaware that cyber-weapons and cyber-warfare pose a real risk to their organizations. As you can see from the chart, less than 5 percent of organizations’ business continuity plans address cyber-attacks, terrorist attacks, computer viruses and biological attacks/pandemics. (Source: Spy-Ops Cyber Warfare unclassified briefing)
Analyzing the Threat
In 2007, a denial-of-service attack was launched every 53 minutes. The 2007 FBI/Computer Security Institute study indicated that loss of revenue attributed to DDoS (dedicated denial of service) was approximately US$90,000 an hour for a retail catalog sales company.
Malware is another common cyber-weapon. Malware (short for malicious software) is a computer program designed with malicious intent. This intent may be to cause annoying pop-up ads with the hope you will click on one and generate revenue, or forms of spyware, Trojans and viruses that can be used to take over your computer, steal your identity, swipe sensitive financial information or track your activities.
At least five new pieces of malware emerge every two minutes, according to Kaspersky’s Internet Security Lab. One critical measure I monitor regularly is the number of significant events reported to Hackerwatch.Org. At the time I’m writing this, in the past 24 hours, there have been more than 8 million significant incidents reported.
The warning signs are there, but the question remains: Are we smart enough to prepare?
“Organizations need to take this threat much more seriously then they are,” said Bob Coxe, senior vice president of Criterion Systems and former Deputy CIO at FEMA (Federal Emergency Management Agency). Security experts have recently raised the level of awareness about the attacks and the threat they pose to the United States. This is clearly a national security issue that demands immediate attention.
Insider reports have indicated that the Bush administration has included $6 billion (in a “black” category) in the budget to address cybersecurity. While this funding should go a long way to securing government computer systems, what about all the business and personal computer systems?
A computer not properly protected is a cyber-weapon waiting to be aimed, armed and fired. STORM is a highly sophisticated cyber-weapon that is thought to have infiltrated up to 80 million computers. The DDoS capacity of a large network of compromised computers like this could easily overwhelm the information infrastructure of small and medium-sized countries, like in the case of the cyber-attack on Estonia that took place in the spring of 2007.
Cables Cuts
Not all cyber-attacks have to come online. Some attacks can manifest themselves in the physical world. On Jan. 30, an undersea telecommunications cable in the Mediterranean was severed, resulting in a dramatic slowdown in Internet access for people and businesses in India, Sri Lanka, Pakistan and much of the Middle East.
In the following weeks, four more cables were cut, two of them in multiple places. Major damage such as this to the Internet backbone can cause significant problems despite the built-in redundancy that allows rerouting of information flow. The loss of this much capacity impacts all users.
Describing a similar incident in 2005, ECT News Network columnist Anthony Mitchell wrote, “Call centers in India that operated solely with Reliance as a telcom and Internet service provider face financial losses, and some are expected to close as a result. Not only have these sole-supplier facilities lost operating revenues, some have lost clients as well.”
At this point no one can definitively say if the damage to the cables was the result of deliberate acts, acts of terrorism or some other yet to be explained circumstances. However, one must admit so many cuts in such a short amount of time are suspicious to say the least.
In Conclusion
Moving from bombs and bullets to bits and bytes has created a business risk and a new weapon in the modern arsenal for warfare. The new risks now include cyber-weapons that are specifically designed to attack and disrupt our telecommunications and information infrastructure and cause significant damage to our economy.
Factors that differentiate between cyber-attacks as a law enforcement and legal issue, versus cyber-attacks as a national security matter, are as clear as mud. When that attack goes international, the issues become even more clouded.
Organizations that do not address this threat in their business continuity plans not only can face claims of negligence and possible shareholder lawsuits, but the impact could be so significant they go out of business.
Kevin Coleman is a strategic management consultant with Technolytics and specializes in security and compliance. He is a former chief strategist for Netscape and a Kellogg School of Management executive scholar with more than 15 years of experience.