Ransomware and distributed denial-of-service attacks significantly increased from October to November of this year, a cybersecurity research company reported Tuesday.
NCC Group reported a 41% jump in ransomware attacks in November, to 265 from 188 in October, making November the most active month for the malware since April.
During the same period in 2021, the report continued, the increase was smaller (4%), but the totals were higher — 314 for October and 328 for November.
That is likely due to the Conti and Pysa gangs being heavy contributors to the ransomware threat landscape at the time, the report said. Both gangs are either dissolved or separated now.
Seasonal variations in ransomware attacks are common, noted Marcus Smiley, CEO of Epoch Concepts, an IT solutions provider based in Littleton, Colo.
“Ransomware attacks have increased during the holiday season since at least 2018,” Smiley told TechNewsWorld.
“The simplest explanation is that companies wind down operations towards the end of the year, making them less responsive to cyberattacks than usual,” he said. “This makes it a logical time to launch new ransomware campaigns.”
“There is definitely an increased risk of attacks during the holiday season,” added Morgan Demboski, a threat intelligence analyst with IronNet, a network security company in McLean, Va.
“Threat actors try to take advantage of a potential lower cybersecurity posture and response due to employees being on break for the holiday,” Demboski told TechNewsWorld.
In 2021, there was a drop in ransomware attacks in the fourth quarter as threat actors focused on quality, not quantity, noted James McQuiggan. a security awareness advocate at KnowBe4, a security awareness training provider in Clearwater, Fla.
“However, this year, there have been increases in attacks targeting health care, education, and retail,” McQuiggan told TechNewsWorld.
A Malware for All Seasons
Attacks, in general, can often be tracked back to particular time periods, which will enable them to either blend in with expected, legitimate communications or to maximize their chances of a large payoff, explained Mark Guntrip, senior director of cybersecurity strategy at Menlo Security, a cybersecurity company in Mountain View, Calif.
“Attacks against agriculture companies around harvest times have prompted warnings from the FBI,” Guntrip told TechNewsWorld. “There have also been attacks against game manufacturers close to a big launch and candy manufacturers before Halloween and holidays.”
While ransomware attacks may have seasonal spikes, experts say the practice will continue to grow no matter what time of year it is.
Ransomware Regional Analysis – November 2022
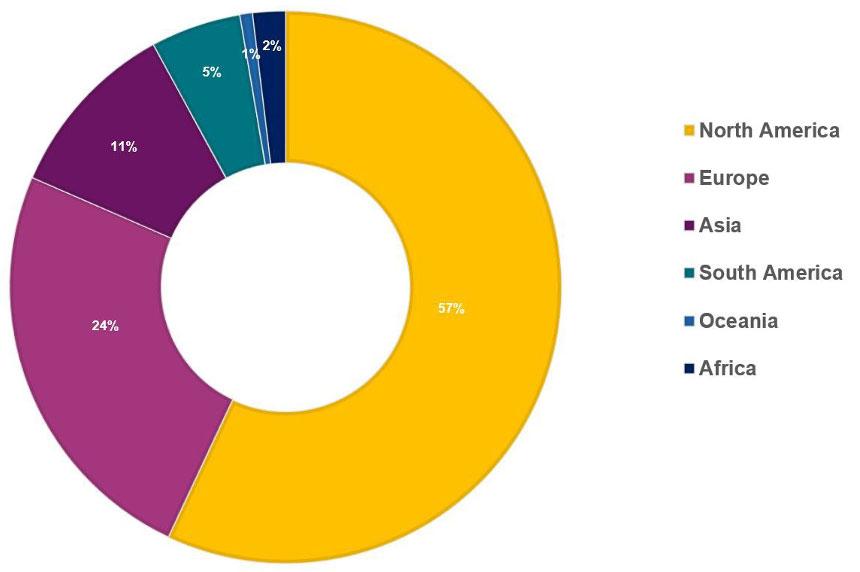
As observed throughout the year, in November the top two regions targeted by ransomware globally remained North America, followed by Europe. (Source: NCC Group Monthly Threat Pulse)
“Ransomware attacks have risen and will continue to rise in 2023,” Guntrip said.
“From attacks on critical infrastructure to individual businesses, it’s clear that in today’s threat landscape, no one’s systems are safe, and there are no signs of cybercriminals slowing down their efforts,” he observed.
“The level of success and subsequent money paid after an attack is an obvious attraction for threat actors to continue to increase their focus on ransomware,” he added.
Extortion Gaining Popularity
Increased opportunity is contributing to rising ransomware attacks, maintained Smiley. “Today’s organizations have more connected surfaces thanks to IoT and remote employment than ever before,” he said.
Another factor is motive. “With rising geopolitical conflict around the world, there is more activity from nation-state and politically driven actors,” he observed.
“Yet another factor,” he added, “is the increased number of ransomware-as-a-service groups who provide their services to less sophisticated cybercriminals for a fee.”
Demboski explained that “as a service” offerings have made ransomware a low-effort, low-risk option for generating criminal gains.
“The availability of various ransomware families via ransomware-as-a-service, paired with other readily available services like phishing-as-a-service and initial access brokers, have made it very easy for cybercriminals to buy credentials and ready-made access to organizations, in essence giving them all the necessary ingredients to launch an effective and damaging ransomware attack,” she said.
A troubling trend that will further fuel ransomware attacks is the use of ransomware for extortion.
“With the ransomware floodgates opening in recent months, there have been many cases of ransoms not being lifted after payment and data being held hostage for future extortion, including double and triple extortion,” said Timothy Morris, chief security advisor at Tanium, maker of an endpoint management and security platform in Kirkland, Wash.
“This makes extortion the trend to keep in mind,” Morris told TechNewsWorld. “It is easier to deal with than the logistics of ransomware keys and managing encryption/decryption, which can create tech support issues that damage the ‘reputation’ of criminals syndicates if they fall short.”
DDoS Attacks Rising
As in October, the NCC report noted, distributed denial-of-service attacks continued to rise, with 3,648 spotted in November. A prime target of those was the United States, with 1,543 attacks.
Reasons for the U.S. being the most targeted include the large attack surface and existing geopolitical tensions in the country, which show no sign of relaxing, the report explained.
Given the timing, the U.S. attacks could have been intended to disrupt the mid-term elections, it added.
NCC’s Global Head of Threat Intelligence, Matt Hull, predicted that DDoS attacks would likely continue to rise.
“However, as more organizations become aware of the increased threat, it will be interesting to see how malicious actors employing DDoS attacks are countered,” he said in a statement. “DDoS is not a new attack type, and preventative and defensive measures are more widely available and affordable than ever before.”
DDoS Not for Ransomware Crowd
While denial-of-service attacks were common with some cybercriminal groups, there has been a reduction in DDoS attacks relating to ransomware, noted McQuiggan.
“This action could be a result of preventing the victim organization from utilizing the internet to get to the Tor network, making it very difficult to pay,” he explained.
“If they do launch the denial of service,” he continued, “it’s to let the organization know that they are still susceptible to other attacks to continue the threat.”
There seems to be less of a concern over DDoS attacks compared with data breaches, malware, and phishing because DDoS attacks typically do not result in the theft or loss of sensitive data, observed Casey Ellis, CTO and founder of Bugcrowd, an operator of a crowdsourced bug bounty platform.
“While DDoS attacks can cause significant disruption to a company’s operations, they do not pose the same level of risk to the confidentiality, integrity, or availability of critical data as other types of cyberattacks,” Ellis told TechNewsWorld. “DDOS attacks are less sophisticated and easier to defend against compared to data breaches, malware, and phishing attacks.”
























































