
The Internet is actualizing the vision of a global village today. Cars are becoming infotainment centers with online connections; printers, home appliances and even door locks are being connected to the Internet; and some cities have begun putting in hundreds of sensors to help them better manage their buildings and utilities.
The world is fast becoming interconnected, in other words, and that helps save money and make things more efficient, according to major players such as IBM and Cisco. It also gives rise to what is called the Internet of Things, also known as the Internet of Everything.
The other side of all this connectivity, however, is a security problem that threatens to overshadow anything we’ve ever seen.
Forget about the NSA spying on everyone everywhere; they’re our madmen and we know where they are. Think instead of the assorted cybercriminals and cyberpranksters who will strike through Internet-connected appliances and cars and disappear before we even know what has happened.
‘An Increasingly Large Attack Surface’
“The Internet of Everything connects things all around us, from baby monitors to TVs and other home appliances,” Alex Watson, director of security research at Websense, told TechNewsWorld.
“These devices run very basic operating systems without the mechanisms for security updates that we expect from our PCs and mobile devices,” Watson continued. “This has created an increasingly large attack surface for criminals to exploit as an initial foothold or vector into otherwise well-protected IT environments.”
Medical devices, connected cars and increasingly networked public safety systems such as dedicated short-range communications for traffic safety present a particularly high level of risk to attack, Watson suggested.
The Global IP-based Village
The IoT, or IoE, is “billions of smart connected things — a sort of universal global neural network in the cloud — that will encompass every aspect of our lives,” states a white paper published jointly by mobile chip maker ARM and semiconductor manufacturer Freescale.
It consists of smart machines interacting and communicating with other machines, objects, environments and infrastructures.
The IoT covers machine-to-machine communications; machine-to-infrastructure communication; telehealth — the remote or real-time pervasive monitoring of patients, diagnosis and drug delivery; continuous monitoring of and firmware upgrades for vehicles; tracking goods on the move; automatic traffic management; remote security and control; environmental monitoring and control; and home and industrial building automation.
The IoE creates more than US$14 million in value due to a combination of increased revenues and lower costs, Cisco says.
Players in the IoT Business
IBM has been actively positioning itself as an IoT player with its Smarter Planet initiative. This includes the company’s Smarter Cities campaign.
The basic idea is, you pay IBM lots of money to put in sensors everywhere and replace your servers and software with its own and pay it a monthly fee to manage these systems and analyze the data they collect. Nice work, if you can get it.
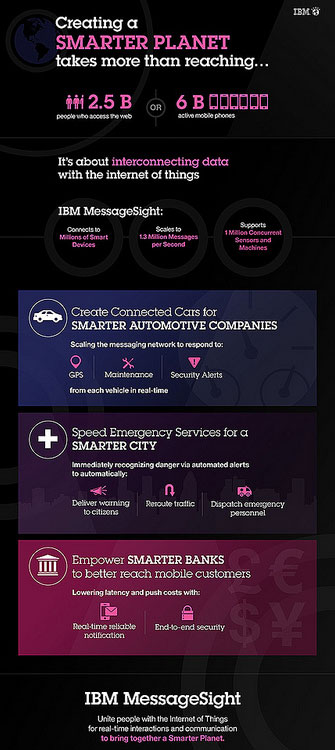
Big Blue is chugging merrily along with these campaigns, turning out supporting products such as MessageSight, an appliance it launched in April to handle M2M communications.
IBM is involved in more than 2,000 projects with cities worldwide to monitor, manage and measure most of their physical systems.
One such city, South Bend, Ind., is using IBM’s Smarter Cities Cloud Analytics to handle its wastewater management system. It expects to save $120 million in infrastructure systems while avoiding costly fines for overflows.
Cisco, meanwhile, is offering the Cisco Open Network Environment, or ONE, portfolio of technologies for the IoT.
Its stance is that the Internet Protocol will replace most of the 92 legacy protocols used today in connected devices. Cisco’s ONE technologies will make those devices programmable.
Separately, 10 companies set up the Internet of Things Consortium in January. Among them are Logitech, Ouya and SmartThings.
Driving While Connected
General Motors in February announced a global strategy to deliver new connected cars and trucks with 4G LTE capability built in. This is a joint venture with AT&T.
Meanwhile, AT&T has gone full tilt into the connected car business. In August, it opened a connected home and car foundry, an innovation and developer collaboration center in Atlanta, Ga. This will focus on the IoT.
A Connected Car Expo will be held at the Los Angeles Convention Center in November, and every major brand will be there. Other participants will include Intel, Qualcomm, the Car Connectivity Consortium, Sprint, AOL, Facebook, Apple, Google, HD Radio, Microsoft, Nuance, Tumblr and Yahoo.
A Connected Cars World Conference will be held in Amsterdam next year.
“The automotive industry understands there is a [security] danger, and they have representatives that participate in some cybersecurity working groups,” Jarad Carleton, a principal analyst at Frost & Sullivan, told TechNewsWorld.

One of the “most frightening” issues is that cars are beginning to offer WiFi for passengers, Carleton said.
“That network connection is a potential route into the control systems for the automobile, many of which are controlled by computer software,” he elaborated. “Things like applying the brakes, accelerating or even turning off the engine while driving at highway speeds are possibilities that hackers are already looking into today.”
Stop, Look and Listen to Your Heart Race
Indeed, “we have already seen cases where people are being exploited — both in terms of basic privacy violations and in some cases for financial gain — as a result of device insecurity,” Kevin O’Brien, enterprise solution architect at CloudLock, told TechNewsWorld.
“Certain devices simply should not be accessible via the Internet because the value added by their connected state is outweighed by the risk created,” he continued.
“There are an increasing number of exploits occurring in more recent times that suggest a quasi-anarchist ‘for the lulz’ approach to hacking,” O’Brien concluded. “By placing highly visible or highly useful systems online, we are apt to see more and more of this behavior.”






















































