Ransomware is the top supply chain risk facing organizations today, according to a survey released Monday by ISACA, an association for IT professionals with 140,000 members in 180 countries.
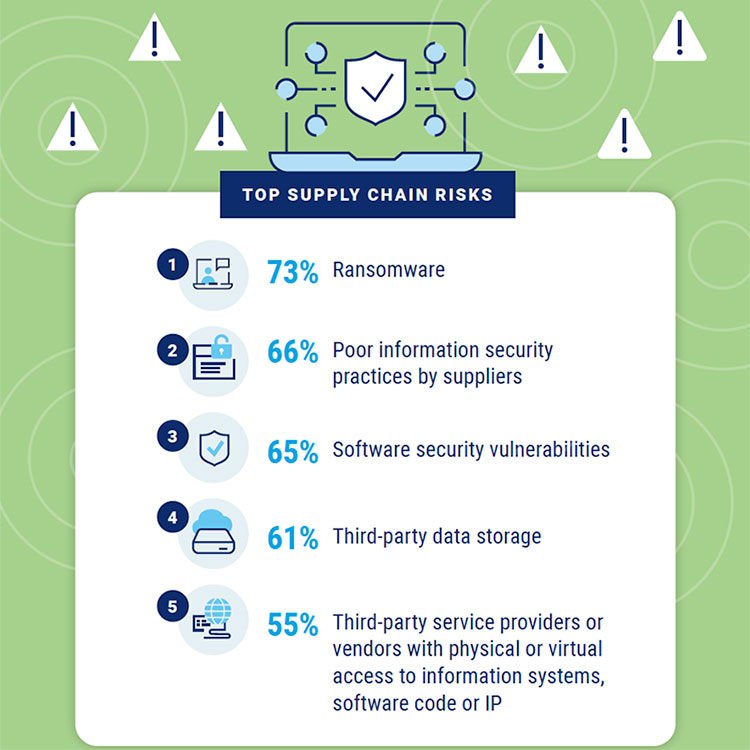
The survey, based on responses from more than 1,300 IT pros with supply chain insights, found that nearly three-quarters of the respondents (73%) said ransomware was a key concern when considering supply chain risks to their organizations.
Other key concerns included poor information security practices by suppliers (66%), software security vulnerabilities (65%), third-party data storage (61%), and third-party service providers or vendors with physical or virtual access to information systems, software code, or IP (55%).
The heightened concern over ransomware might be because it can have a double whammy on an organization.
“First, there is the risk of an attacker finding an attack pathway into an organization from a compromised vendor or software dependency, as we saw with the SolarWinds and Kaseya attacks that affected a massive number of downstream victims via that supply chain,” explained Chris Clements, vice president of solutions architecture at Cerberus Sentinel, a cybersecurity consulting and penetration testing company in Scottsdale, Ariz.
“Then there are secondary effects,” he continued, “where a ransomware gang may steal data stored at a third-party provider and attempt to extort both organizations by threatening to publicly release it if a ransom isn’t paid.”
“The other side of the coin is that a ransomware attack on an organization’s supply chain can cause significant operational disruption if the third party it depends on is unable to provide services due to the cyberattack,” he told TechNewsWorld.
Leader Ignorance
Those attacks on the software supply chain can have a ripple effect on the physical supply chain. “Ransomware contributes to significant disruptions in an already taxed supply chain when systems that manage the manufacture and distribution of goods and services are taken offline,” observed Erich Kron, security awareness advocate for KnowBe4, a security awareness training provider in Clearwater, Fla.
“This can impact ordering and tracking of inventory of the materials needed to make items, impact the status tracking of items needed to fill orders and can create logistical problems getting materials to customers, creating shortages for their customers,” he told TechNewsWorld.
“In a world of just-in-time order fulfillment, any delays can cascade down the supply chain, impacting more and more people along the way,” he added.
Nearly a third of the IT pros surveyed (30%) revealed that the leaders in their organizations did not have a sufficient understanding of supply chain risk. “The fact that it was only 30% was somewhat encouraging,” ISACA Board Director Rob Clyde told TechNewsWorld. “A few years ago, that number would have been far higher.”
“I think a lot of the ignorance comes from simply vastly underestimating the number of dependencies and their criticality to an organization’s operations,” Clements said.
“These third-party tools, by their nature, often require administrative rights to many if not all a customer’s devices that they interact with, meaning a compromise of just one of these vendors may be enough to completely compromise their customer’s environments as well.”
“Similarly, there is often ignorance of just how much many organizations depend on third-party vendors,” he continued, “Most organizations I know don’t have a ready-to-go fallback plan if a major provider such as their email communications platform were to have an extended outage.”
Pessimistic Vein
Even in situations where leaders do understand the risks to their supply chain, they won’t err on the side of security. “In situations where companies have to choose between security and growth, every time you will see them choosing growth,” observed Casey Bisson, head of product and developer relations for BluBracket, a cybersecurity services company in Menlo Park, Calif.
“That comes at the risk of their customers. That comes at the risk of the company itself,” he told TechNewsWorld. “But increasingly, we’re starting to see executives being held responsible for those choices.”
The ISACA survey also found a strong vein of pessimism among the IT Pros about the security prospects of their supply chains. Only 44% indicated they have high confidence in the security of their organization’s supply chain, while 53% expect supply chain issues to remain the same or get worse over the next six months.
Source: ISACA | Understanding Supply Chain Security Gaps | 2022 Global Research Report
One of the more surprising findings of the survey was that 25% of the organizations said they’d experienced a supply chain attack in the last 12 months. “I did not think it would be anywhere near that high,” Clyde said.
“While many organizations have experienced cyberattacks in the last 12 months, I didn’t think there would be this many attributing it to a supply chain problem. If we asked that question several years ago, that would have been a very low number,” he added.
Meanwhile, more than eight out of 10 of the tech experts (84%) said their supply chains needed better governance than what they have now.
“The way we try to certify supply chain partners today just doesn’t work,” maintained Andrew Hay, COO of Lares, an information security consulting firm in Denver.
“We either generate an arbitrary score based on external scan data and IP-based confidence or we try and force them to fill out 100 or more questions on a spreadsheet,” he told TechNewsWorld. “Neither accurately depicts how secure an organization is.”
Auditing Needed
Mike Parkin, a senior technical engineer with Vulcan Cyber, a provider of SaaS for enterprise cyber risk remediation in Tel Aviv, Israel, noted that there are multiple factors that come into play when trying to secure the supply chain.
“Organizations only ever have full visibility into their own environment, which means they have to trust their vendors are following best practices,” he told TechNewsWorld. “This means they need to include contingencies for when a third-party vendor is breached or build a process that severely restricts the damage that can occur if it does happen.”
“That’s even more complicated when an organization needs to deal with multiple vendors to compensate for shortages or disruptions,” he continued. “Even with the correct risk management tools, it can be hard to account for everything in play.”
Kron added that there has to be some trust in suppliers; however, if governance is increased to confirm what organizations tell us, as opposed to just trusting answers from a questionnaire, a system of auditing has to be put in place.
“This will inevitably increase costs, something that many organizations work hard to keep as low as possible in order to remain competitive,” he said.
“While this may be easier to justify for critical government or military systems, it can be a tough sell for traditional suppliers,” he maintained. “To add to the challenges, enforcing governance on foreign suppliers of goods and materials may be difficult or impossible to achieve. This is not an easy challenge to tackle and will continue to be a topic of discussion for quite some time.”























































