Sensitive data in unstructured formats (e.g., in documents and file systems) poses a distinct problem to security- and compliance-minded organizations, a problem exacerbated by the ubiquity of Web-based portals and collaborative tools such as Microsoft SharePoint.
Based on the responses of more than 160 companies in the June 2009 benchmark study, “Securing Unstructured Data: How Best-in-Class Companies Manage to Serve and Protect,” this research brief describes how current Microsoft SharePoint users respond to the security challenges raised by their expanding reliance on collaboration.
Business Context: SharePoint as Comedy or Tragedy?
In its classic form, the tragedy of the commons is illustrated by a scenario in which a shared pasture is freely available to all citizens for grazing their livestock. When acting from their individual self-interests, each citizen logically concludes that they should increase their herd. The tragedy of this scenario is that it inevitably leads to too many animals grazing, depleting the resources of the shared pasture to the detriment of all. As Garrett Hardin wrote in Science magazine (December 1968), “Ruin is the destination toward which all men rush, each pursuing his own best interest.”
Notions from the traditional world of physical property, however, do not always run parallel in the Internet-enabled, digitally-based world of intellectual property. For example, often the value of a digital resource can dramatically increase as the result of more individuals using it — a scenario dubbed by Carol Rose as the comedy of the commons in the University of Chicago Law Review (1987). In other variants, especially those popularized by Stanford University professor Lawrence Lessig, each individual participant adds to the intellectual commons, thereby enriching the resources available to all.
Aberdeen’s benchmark study on “Securing Unstructured Data” (June 2009) highlights the ease with which unstructured data can be copied and shared between end-users throughout the extended enterprise. For security- and compliance-minded organizations, however, collaboration tools such as Microsoft SharePoint make it even easier to scatter sensitive information to unintended recipients, dramatically increasing the likelihood of data loss or data exposure. In this sense, Aberdeen’s research shows that the current use of Microsoft SharePoint illustrates both the comedy (collaboration) — and the tragedy (loss or exposure of sensitive data) — of the commons. The biggest challenge with protecting and managing unstructured data is that it has steadily become so important — and so easy — to share.
A Closer Look at Current SharePoint Users
A closer analysis of current SharePoint users shows that many install complementary IT Security technologies in an effort to gain more control over their unstructured data (Figure 3). However, in addition to the selection and use of these technologies, to achieve Best-in-Class performance companies must also educate their end-users about security and shape their corporate culture with respect to sharing, protecting and managing their sensitive unstructured data.
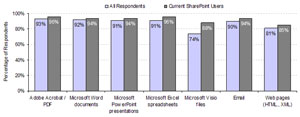
Out of more than 160 companies participating in the June 2009 benchmark study on “Securing Unstructured Data,” 70 indicated that they are current users of Microsoft SharePoint. The research confirms that SharePoint eases intra-organizational collaboration, and showed that 82 percent of SharePoint users actually increased the volume of unstructured data created on a year-over-year basis, by an average of about 14 percent. Not surprisingly, this was especially true for Microsoft-centric sources of unstructured data such as Microsoft Office documents, spreadsheets and presentations, as well as email and Web pages (Figure 1). This leads to an upward spiral, in which more widespread collaboration is fueled by a greater volume of unstructured data, and increasing numbers of end-users are being granted access privileges.
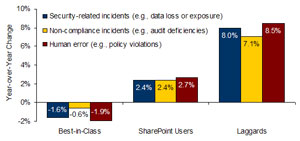
Although the SharePoint solution does include many security-related features, the decentralized, organic growth of SharePoint servers which is typical for most companies means that these capabilities are utilized inconsistently at best. Over the last 12 months, current SharePoint users were below the Industry Average in terms of data loss or data exposure incidents, audit deficiencies, and human error leading to policy violations with respect to unstructured data (Figure 2).
In each of these metrics, SharePoint users went in the wrong direction — i.e., they experienced a year-over-year increase. On the bright side, their results were better than those of the Laggards (bottom 30 percent) in the study.
SharePoint Users’ Capabilities and Enabling Technologies
A closer analysis of current SharePoint users shows that many install complementary IT Security technologies in an effort to gain more control over their unstructured data (Figure 3). For two technologies in particular — full-disk encryption, and data discovery tools — current SharePoint users are more likely to have deployed than even the Best-in-Class.
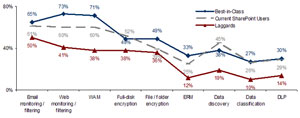
However, in Aberdeen’s benchmark-based research methodology, use of SharePoint or complementary technologies such as data discovery or encryption is only one part of the overall story. Since the same technologies are equally available to everyone, the fact that some companies are able to achieve significantly better results than others also lies partly in the policy, planning, process and organizational elements of ongoing operations. As specific examples of the gaps in these capabilities between SharePoint users and the Best-in-Class, SharePoint users in Aberdeen’s study were:
- 28 percent less likely to discover and classify unstructured data
- 13 percent less likely to monitor, audit and report on end-user access to sensitive unstructured data
- 12 percent less likely to systematically eliminate root causes for exceptions, security events or incidents of non-compliance
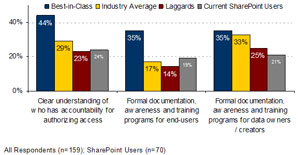
SharePoint users are Laggards in terms of establishing a clear understanding of who has accountability for authorizing access to sensitive unstructured data (Figure 4), largely as a result of an environment in which individual document creators typically define access privileges, or accept those inherited by default. SharePoint users also lag significantly in terms of investing in documentation, awareness and training programs for end-users. Even more worrying is the lack of formal documentation, awareness and training programs for data owners / creators. These findings are at odds with common sense — how can people be expected to do the right thing if they are not trained and reminded of what that is? — and yet in absolute terms the investments in such training are made by just one-third (35 percent) of the Best-in-Class. Meanwhile nearly all (97 percent) of current SharePoint users indicated that individuals were “typically” or “sometimes” left to determine the access privileges to the unstructured data which they created. This is one root cause of the tragedy of the commons.
Case in Point: Global Leader in Specialty Materials
The success of a world leader in high-tech specialty materials with more than 150 years of corporate history is supported not only by its expertise in materials, manufacturing and process engineering, but also by a century of tradition in formal research and development. With 2008 revenues approaching US$6 billion, the company has more than 50 manufacturing plants in 15 countries. Some 3,000 of the company’s approximately 27,000 full-time employees are in the R&D group, which manages several terabytes of unstructured data that represents the core intellectual property of the company. About 2,000 of these R&D employees use Microsoft SharePoint.
Previously, the R&D group had tried unsuccessfully to collaborate using OpenText’s Livelink. “This was a disaster, because the product didn’t look and work like Microsoft; we are a big Microsoft shop,” said the group’s head of knowledge management and information protection. “Even though we had already made a substantial investment, in the end, that project was written off.” A separate effort to use EMC’s Documentum met with a similar fate: “It was incredibly difficult to use, and consequently nobody used it.” This is not to say that the current use of SharePoint has been without its challenges. The group uses SharePoint 2007 and Microsoft Office 2003, and “the interface between these two generations of products is miserable. But a corporate-level decision was made that didn’t see any reason to cost-justify an upgrade beyond Office 2003, except for SharePoint 2007.”
Such issues aside, the group is seeing a “constant flow of materials from file shares to SharePoint,” and the consistency of their global SharePoint structure “nicely facilitates collaboration.” In the last year, some of that collaboration has also started to go external, in the sense of enabling access for research colleagues at universities, joint ventures, and third-party partners.
One thing that sets this R&D organization positively apart in terms of best practices is in the way it addresses the fundamental training that SharePoint site owners need to have to be successful in protecting and managing their sensitive data. The company’s R&D group has a long history of establishing “communities of practice,” which meet on a regular basis to facilitate best practices and the sharing of information. With respect to SharePoint, monthly training sessions — at both the “Beginner” level and the “Expert” level — regularly draw groups of 50 to 80 people. “Occasionally you’ll hear someone say ‘give me the book on SharePoint,'” the group’s head of knowledge management and information protection notes wryly. “But the stark reality is that there isn’t one. It’s really a collaborative environment that people can use as a tool to solve the problems they’re looking to solve.”
Over its long and successful history, the company has taken pride in tackling the toughest problems, imagining the possibilities, and turning those possibilities into breakthrough realities. By leveraging solutions such as Microsoft SharePoint, the company’s strong collaborative culture continues to drive it forward.
Summary and Recommendations
Regardless of the specific technology used in support of collaboration using unstructured data, Aberdeen’s research has consistently shown that the following general steps are consistent with top performance: ol.thisol { font-weight:bold } ol.thisol span {font-weight:normal }
- Identify and classify your data. You can’t protect what you don’t manage, and you can’t manage what you don’t know about.
- Prioritize your security control objectives for these information assets as a function of risk, audit and compliance requirements. Not all data is worth being protected; you should prioritize the protection of the data with the greatest impact on the business.
- Establish consistent policies as part of an overall approach to safeguarding sensitive data at rest in the back-end, in flight on the network, and in use at the endpoints. Data is flowing everywhere, all the time.
- Select and deploy data protection solutions, which will likely include a combination of enabling technologies, including collaboration tools, content management, access management, encryption and key management, enterprise rights management, DLP, and other content monitoring / filtering solutions.
- Invest in documentation, awareness and training for end-users and content creators, who should be made fully aware of their responsibilities for protecting the organization’s sensitive data. Investments in technologies to help protect data can be significantly eroded by insufficient investments in the people and process side of successful implementation.
- Assign clear ownership and accountability for data protection initiatives to an executive or cross-functional team. The “one throat to choke” principle is highly correlated with the achievement of top results.
- Automate enforcement of policies whenever reasonable, with notification to end-users; standardize audit, analysis and reporting. Both will reinforce awareness of policies and expectations for behavior.
- Measure and monitor regularly; drive continuous improvements by finding and eliminating root causes for exceptions, security events and audit deficiencies.
Every organization is somewhere along this path, and for the business-oriented purchaser / decision maker, this list should be helpful in asking the right questions, both internally and externally (e.g., of product and services providers), about proposed solutions and implementation plans.
Explicit acknowledgment of the need to support collaboration as a driver for current investments in protecting and managing unstructured data underscores the slow but steady shift in the perception of IT Security from one of being an obstacle, to one of being an enabler.
In addition to the selection and use of collaborative technologies such as Microsoft SharePoint, to achieve Best-in-Class performance companies must also educate their end-users about security and shape their corporate culture with respect to sharing, protecting and managing their sensitive unstructured data. Over time, the most successful initiatives will achieve this non-technical outcome — changing the company’s culture regarding data protection — which is perhaps the most difficult one to achieve of all.
Derek Brink is a vice president and research fellow at Aberdeen Group. Max Gladstone is a research associate at Aberdeen.