
2006 witnessed the beginning of a convergence between physical and IT security, driven largely by the greatest fear of security professionals — a coordinated assault that combines an attack on the IT network to eliminate an organization’s ability to command, control and communicate with a physical security attack.
In order to get a firm grasp of an organization’s overall security posture, it is increasingly important to integrate all of your various physical and IT security systems — systems that until now have been managed and run in separate silos.
For an organization to adequately protect itself from today’s increasingly sophisticated threats, it’s critical to leverage advancements in technologies that cater to both physical and IT environments.
Video Revolution
In addition to the convergence of physical and IT security systems, the convergence continues in video technologies as well — IP video technologies (DVRs, NVRs, cameras, etc.) are quickly being assimilated into the technology infrastructure.
Camera, sensor and alarm technologies have become less and less expensive and easier to deploy, giving security personnel wide-reaching insight into the physical surroundings.
Research and Markets expects the market for video surveillance equipment to grow by 37 percent by 2009, as companies that converge physical and IT security take the blinders off as they deploy a complete network of surveillance technologies that communicate in real-time to deliver operations center personnel true situational awareness.
However, the constantly growing number of cameras, sensors and alarms creates an additional scalability issue — the amount of data and feeds to watch and analyze can be overwhelming, leading to the question, “How can one have 1,000 eyes and still be blind?”
The challenge now becomes the ability to manage a variety of analog and digital systems that can intercommunicate.
All of these converged security technologies can produce a greater amount of information from which to make security decisions. From here, it is crucial to be able to manage, correlate and analyze the information to drive the right response, making it critical to have a platform that can manage all of this information effectively and help produce decisions quickly.
Securing the Borders
The simple reality is that now that the world is changing, the ways in which you must deal with security threats are changing too.
We’ve entered a significant shift in the security field — a convergence of traditionally separate physical and IT security systems. 4A International indicates that the US$120 billion physical security market is undergoing a tectonic shift, driven largely by integration with IT security systems.
In addition, according to market research firm the Freedonia Group, the global market for private security products and systems is forecast to grow 8 percent annually through 2010, reaching $85 billion.
Take the Secure Border Initiative, also referred to as SBInet, for example. Some estimate the value of the multiyear contract at more than $2 billion, which will be used to install new tracking sensors, cameras and communications equipment along the border of the United States.
The SBInet program is just one large-scale example — enterprises and municipalities around the globe are investing in these systems.
However, at the same time, they won’t abandon their existing network infrastructure — much of which is analog video communications, driven by the dozens to hundreds of network surveillance cameras they’ve installed over the years.
Spanning All Levels of the Enterprise
Security convergence reaches far beyond the technology that enables a greater awareness of security posture, and the shift is upon us. The key is to manage this transition effectively to achieve the results a converged security system promises. This convergence is happening across the following levels:
- Organizational — Reorganization is happening under the risk management umbrella. Now, there is a single organization responsible for all security related activities — whether physical or IT — enabling a coordinated view of the situation and prompting the right response to a given event.
- Facility — The facility is evolving as well. Through highly connected facilities, sophisticated software and collaboration technology, organizations are able to better manage a collocation facility or a virtual location — adding to the need to manage the flow of information and response.
- Physical Security and Video Technology — New video technologies are enhancing the abilities to protect the physical realm. However, this wave of new technologies must co-exist and work seamlessly with existing video solutions. Enterprises face an interesting proposition if they manage this convergence correctly — benefiting from new innovations while leveraging established assets.
- Physical and Logical/IT — Connecting network and IT access to systems and applications with the physical access of a facility, building and/or room is gaining significant interest, with major physical security players partnering with logical security vendors to broaden protection from people and assets to information and infrastructure.
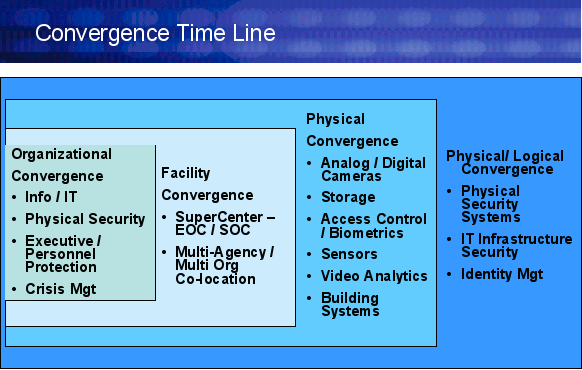
All of these levels are converging upon each other to create a new centralized view of security across an organization, bringing with it a number of technology challenges that must be acknowledged and addressed. To illustrate, consider these key technology convergence issues security organizations face as they strive to meet their primary mission of protecting people, assets and infrastructure:
- Analog to Digital Migration — Organizations have to manage a large installed base of analog (90 percent-plus) plus fast-emerging digital solutions.
- Multiple Management Systems — Every product and system has a proprietary standalone management console.
- Data Overload — There are too many cameras to monitor and too many data sources.
- Disparate Equipment and Systems — Systems such as surveillance, access control, information security, etc. to date have been built in silos and do not interoperate.
- Proactive Mitigation — Forensics only helps “solve” the crime, and does not accomplish the primary mission of preventing it.
- Legacy Equipment and Networks — Forklift upgrades are unrealistic and simply aren’t acceptable.
- Archive and Storage — Legacy tape systems are not suitable for fast data retrieval or event correlation.
- Lack of Standards — Control plane systems do not operate on known standards.
Until now, there has been a void in the physical security market at the intersection of IT security. Despite the staggering number of cameras, alarms and sensors feeding data to an operations center, there lacked a physical security information management platform that could take in all the data, correlate it with data from IT security systems, and provide security personnel the insight to make effective decisions and respond to security events.
Security event management (SEM) and security incident management (SIM) are synonymous in the IT security field, and have long served as the correlation engine that enables an IT security manager to ferret out false alarms and false positives from true events that require attention and response.
SEM enables organizations to pull data from firewalls, intrusion detection and prevention systems, antivirus software and log files to create a clearer view of network activity and how to respond swiftly and effectively.
Companies are now applying these concepts to the physical security field, producing greater insight into what is going on around the facility, and how to best handle a given situation.
By correlating the data feeds and alarms from various sources, a physical security information management (PSIM) solution can provide the context that enables the right response to real threats and security events and disregard those that are false alarms or not real threats.
One Consolidated, Correlated View
This emergence of the PSIM market will provide great value to today’s security organizations.
By converging video surveillance and other physical security systems with IT security, taking in the enormous load of information and distilling it into the most pertinent insight, organizations can significantly improve cross-organization communications and efficiencies while fortifying a comprehensive security posture. The devil is in the details, however.
Many vendors, whether physical security or IT security, will develop their own proprietary solutions that require expensive tie-ins with other products they offer.
The prime value that a PSIM solution can unleash is when it is standards-based and can interconnect an organization’s existing proprietary systems — be it analog or digital, cameras or alarms, firewalls or intrusion prevention systems — enabling the organization to leverage and build off its existing investments rather than a rip-and-replace approach.
The shift towards an integrated physical and IT security system is underway with the convergence of analog and IP video and other data sources into a physical correlation environment that leverages an organization’s existing technology investments.
As companies get more comfortable with the inevitability and value of a fully-integrated physical and IT security environment, the developing PSIM market will blossom into a full solution category segment that will enable security personnel to manage the flood of new threats emerging daily.
Tony Lapolito is vice president of marketing for VidSys.











































